Airgap Workflow
Workflow Diagram
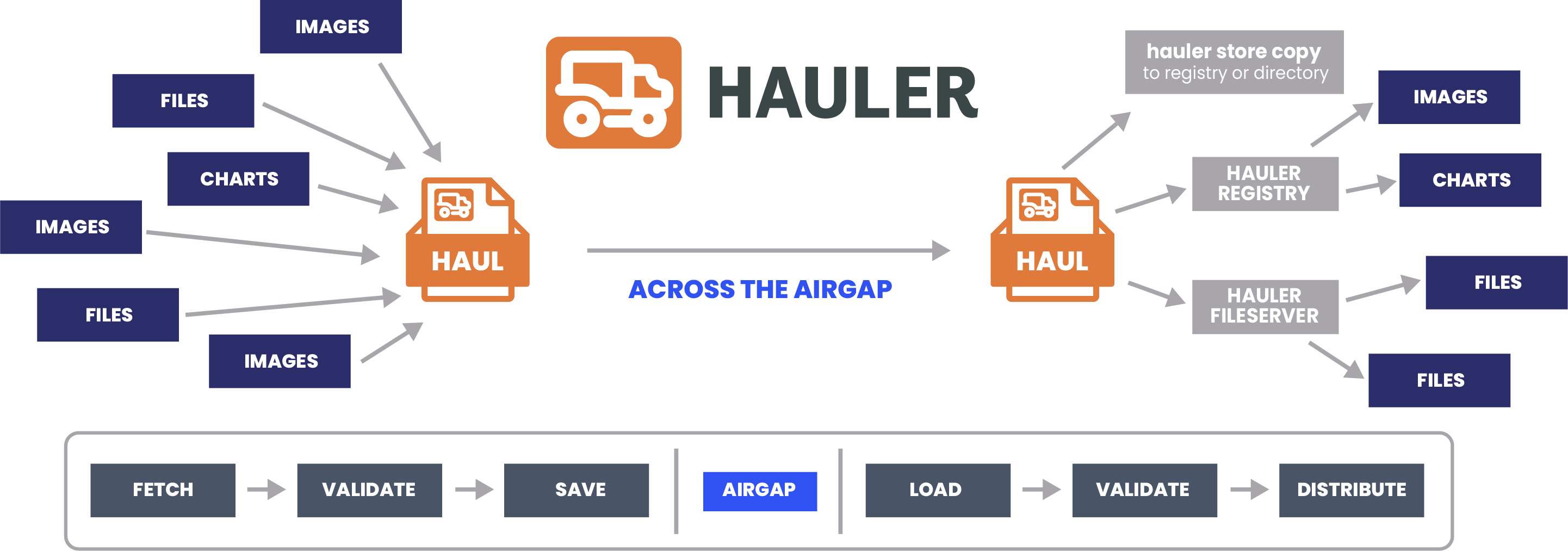
What's an Airgap?
An airgap is a highly secure environment that is physically isolated from external connectivity (usually the internet), ensuring complete isolation from other environments by preventing unauthorized access or data transfers.
Example Use Cases
- Government and Military: These airgaps protect sensitive government and military information and critical defense infrastructure, ensuring that classified data remains secure and inaccessible to unauthorized entities.
- Critical Infrastructure: These airgaps secure power grids, water supply systems, and transportation networks from cyber threats, shielding them from potential disruptions and ensuring their continuous operation.
- Financial Institutions: These airgaps safeguard financial transactions and customer data from cyberattacks, maintaining the trust and integrity of financial systems.
- Research Facilities: These airgaps protect valuable research data, intellectual property, and proprietary information, preserving the integrity and confidentiality of research efforts.
Challenges of an Airgap
- Data Transfers: Transferring data in and out of an airgapped system is complex due to the lack of network connectivity, often necessitating the use of physical media, trusted intermediaries, and meticulous approval processes to ensure data security.
- Usability vs. Security Balance: Balancing security with usability in airgapped environments can be intricate, as the limited convenience poses challenges for user interactions and system operations.
- Maintenance Complexity: Regular system updates, package and dependency updates, and overall maintenance can be challenging in airgapped systems, as the limited network connectivity complicates the process, requiring meticulous planning and execution.
- Costly Implementation: Implementing and maintaining airgapped systems can be costly, demanding specialized workflows, protocols, and security measures to uphold the system's integrity and security.